Addressing the Vulnerability of Data Routing in IoT Network based on Optimization Techniques and Advanced Blow Fish Encryption
DOI:
https://doi.org/10.58564/IJSER.3.1.2024.142Keywords:
blow fish encryption, trust, throughput, Cipher Block Chaining, delayAbstract
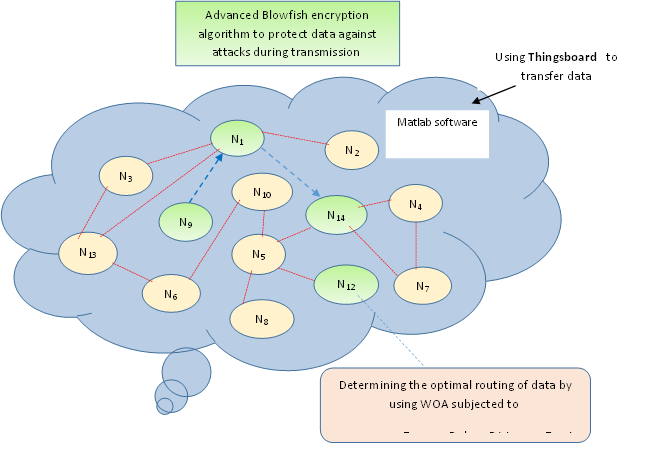
This study focuses on evaluating the data routing protocol in the Internet of Things (IoT). The evaluation is conducted using the Whale Optimization Algorithm (WOA), enhanced by the advanced Blowfish encryption algorithm. In this study, Cipher Block Chaining (CBC) is employed to improve the typical Blowfish technique. Furthermore, several key factors, including the rate of energy consumption, trust, distance, and delay, are considered to ensure the effectiveness of data routing. To demonstrate the feasibility of the proposed approach, four other schemes are utilized in a comparative study. These schemes are particle swarm optimization (PSO), secure routing protocol ( SARP),Genetic algorithm (GA), QoS-based Cross Multi-sink Routing protocol (QCM2R). The results clearly demonstrate the feasibility of the proposed approach when compared to the aforementioned schemes, with the lowest energy consumption, distance, and delay recorded as 0.44325 Joule, 0.43257 meters, and 1.35 x 10-9 seconds, respectively. Additionally, the trust level is the highest at 0.71255, and the throughput reaches its peak at 2.30 Megabytes/ms when the data size is 7 KB. In terms of security dimension, the proposed improved Blowfish encryption technique is compared with Advanced Encryption Standard (AES), Rivest–Shamir–Adleman (RSA) and typical Blow fish algorithm (BFA) encryption techniques to assess its security robustness against Chosen-Ciphertext Attack (CCA) and Chosen-Plaintext Attack (CPA) with varying the size of data bits from 5KB, 7 KB and 10KB. The obtained results show that the proposed improved blow fish approach outperforms three aforementioned schemes with the smallest similarity between unique text and hacked text under CCA and CPA. Furthermore, the least time of decryption occurs with the proposed approach compared to other three schemes.
References
H. P. Nguyen, P. Q. Le, H. Pham, V., X. P. D. Balasubramaniam, and, A. T. Hoang ,“Application of the Internet of Things in 3E (efficiency, economy, and environment) factor-based energy management as smart and sustainable strategy”, Energy Sources, Part A: Recovery, Utilization, and Environmental Effects, vol.1, no.3,pp.1-23, 2022. DOI: https://doi.org/10.1080/15567036.2021.1954110
F. Irudaya, and M. Appadurai,. “Internet of things-based smart transportation system for smart cities”, In Intelligent Systems for Social Good: Theory and Practice , vol.1, pp. 39-50,2022. DOI: https://doi.org/10.1007/978-981-19-0770-8_4
M. N. Mohammed, S. F. ,Desyansah , S. Al-Zubaidi, and E. Yusuf, “An internet of things-based smart homes and healthcare monitoring and management system”, In Journal of physics, vol. 1450, no. 1, pp. 12-79, 2020. DOI: https://doi.org/10.1088/1742-6596/1450/1/012079
B. T. Atiyha, S. Aljabbar, A. Ali,, and A. Jaber, ,“An improved cost estimation for unit commitment using back propagation algorithm”. Malaysian Journal of Fundamental and Applied Sciences, vol.15, no.2, pp.243-248, 2019. DOI: https://doi.org/10.11113/mjfas.v15n2.1146
D. T. Nguyen, X. P. Nguyen, T. D. Hidayat,, R. Huynh and D. T. Nguyen, “A review on the internet of thing (IoT) technologies in controlling ocean environment.” , Energy sources, Part A: Recovery, utilization, and environmental effects, vol.10, no.1, pp. 1-19,2021.
S. R. Zahra, and M. A. Chishti, “Smart Cities Pilot Projects: An IoT Perspective”, Smart Cities: A Data Analytics Perspective, vol.5,no.3, pp.231-255,2021. DOI: https://doi.org/10.1007/978-3-030-60922-1_12
R. Khebbache, A. Merizig, K. Rezeg, and J. Lloret, “ The recent technological trends of smart irrigation systems in smart farming: a review”, International Journal of Computing and Digital Systems, vol.14, no.1, pp.1-25,2023. DOI: https://doi.org/10.12785/ijcds/1401104
A. Goel, and S. Gautam, “ Green IoT: Environment‐Friendly Approach to IoT” , Advances in Data Science and Analytics: Concepts and Paradigms, vol.1, no.3, pp.247-274.,2023. DOI: https://doi.org/10.1002/9781119792826.ch11
F. Zijie, M. A. Al-Shareeda, M. A. Saare, S. Manickam, and S. Karuppayah, “Wireless sensor networks in the internet of things: review, techniques, challenges, and future directions” Indonesian Journal of Electrical Engineering and Computer Science, vol.31,no.2, pp.1190-1200,2023. DOI: https://doi.org/10.11591/ijeecs.v31.i2.pp1190-1200
S. Khriji, Y Benbelgacem., R Chéour, D. E. Houssaini, and O. Kanoun, “ Design and implementation of a cloud-based event-driven architecture for real-time data processing in wireless sensor networks”, The Journal of Supercomputing, vol.1,no.1 ,pp.1-28,2022.
S. Lata, S. Mehfuz, and S. Urooj, “ Secure and reliable wsn for internet of things: Challenges and enabling technologies”, IEEE Access, vol.9, no.1, pp.161103-161128,2021. DOI: https://doi.org/10.1109/ACCESS.2021.3131367
M. Angurala, “ A Review on Energy Efficient Techniques for Wireless Sensor Networks”,International Journal of Intelligent Systems and Applications in Engineering, vol.11,no.8, pp.171-182,2023.
A. M. Fadhil, H. N. Jalo, and O. F. Mohammad, “Improved Security of a Deep Learning-Based Steganography System with Imperceptibility Preservation” International journal of electrical and computer engineering systems, vol.14,no.1, pp.73-81,2023.
D. J. Bahadur, and L. Lakshmanan, “ Enhancement of Quality of Service Based on Cross-Layer Approaches in Wireless Sensor Networks”, Journal of Theoretical and Applied Information Technology, vo.100,no.1,pp.1-19,2022.
M. Afsar, M. H. Tayarani, and M. Aziz, “An adaptive competition-based clustering approach for wireless sensor networks” Telecommunication Systems,vol. 61, no.1,pp.181-204,2016. DOI: https://doi.org/10.1007/s11235-015-9972-1
A. Hamzah, M. Shurman, O. Al-Jarrah, and E. Taqieddin, “ Energy-efficient fuzzy-logic-based clustering technique for hierarchical routing protocols in wireless sensor networks”, Sensors, vol.19,no.3,pp. 561,2019. DOI: https://doi.org/10.3390/s19030561
D. R. Edla, M. C. Kongara, and R. Cheruku , “ A PSO based routing with novel fitness function for improving lifetime of WSNs”, Wireless Personal Communications, vol. no.104, pp. 73-89,2019. DOI: https://doi.org/10.1007/s11277-018-6009-6
D. G. Zhang, H. L. Niu, and S. Liu , “ Novel PEECR-based clustering routing approach”, Soft Computing, vol.21, pp.7313-7323,2017. DOI: https://doi.org/10.1007/s00500-016-2270-3
H. El Alami, and A. Najid , “ Fuzzy logic based clustering algorithm for wireless sensor networks”, In Sensor Technology: Concepts, Methodologies, Tools, and Applications, vol.5,no.1, pp. 351-371,2020. DOI: https://doi.org/10.4018/978-1-7998-2454-1.ch018
H. El Alami, and A. Najid , “ ECH: An enhanced clustering hierarchy approach to maximize lifetime of wireless sensor networks” Ieee Access, vol.7, no.1 ,pp.107142-107153,2019. DOI: https://doi.org/10.1109/ACCESS.2019.2933052
M. Conti, P. Kaliyar, M. M. Rabbani, and S. Ranise, “Attestation-enabled secure and scalable routing protocol for IoT networks”, Ad Hoc Networks, vol.98, no.1,pp20-54,2020. DOI: https://doi.org/10.1016/j.adhoc.2019.102054
W., Rehan, S., Fischer, M. Rehan, Y. Mawad, and S.Saleem, “QCM2R: A QoS-aware cross-layered multichannel multisink routing protocol for stream based wireless sensor networks”, Journal of Network and Computer Applications, vol.156, no.1, pp. 25-52,2020. DOI: https://doi.org/10.1016/j.jnca.2020.102552
Z. Chen, W. Zhou, S. Wu, and L. Cheng , “ An on demand load balancing multi-path routing protocol for differentiated services in MWSN”, Computer Communications, vol.179, pp.296-306,2021. DOI: https://doi.org/10.1016/j.comcom.2021.08.020
I. B. Prasad, S. S. Yadav, and V. Pal , “ HLBC: A hierarchical layer-balanced clustering scheme for energy efficient wireless sensor networks” , IEEE Sensors Journal, vol.21,no.22, pp.26149-26160,2021. DOI: https://doi.org/10.1109/JSEN.2021.3114506
A. M. Fadhil, “ Bit inverting map method for improved steganography scheme”, Diss. Universiti Teknologi Malaysia,2016.
A. Protopsaltis, P. Sarigiannidis, D. Margounakis, and A. Lytos, , “ Data visualization in internet of things: tools, methodologies, and challenges” In Proceedings of the 15th international conference on availability, reliability and security ,pp. 1-11,Augest,2020. DOI: https://doi.org/10.1145/3407023.3409228
V. Jaganathan, B. Palanisamy, and M. Milanova, “Recent trends and techniques in computing information intelligence” The Scientific World Journal, vol.1,no.1, pp.1-23,2016. DOI: https://doi.org/10.1155/2016/7168519
T. Yang, X . Xiangyang, L. Peng, L .Tonghui, and P. Leina, “ A secure routing of wireless sensor networks based on trust evaluation model”, Procedia computer science, vol.131,,no.1,pp. 1156-1163,2018. DOI: https://doi.org/10.1016/j.procs.2018.04.289
S. K. Sarma, “ Energy aware cluster based routing for wireless sensor network in IoT: Impact of bio-inspired algorithm” In 2020 Third International Conference on Smart Systems and Inventive Technology (ICSSIT) ,pp. 198-206, August, 2020. DOI: https://doi.org/10.1109/ICSSIT48917.2020.9214156
L. P. Klimaschewski, “Introduction to Brain Development: Why do We Need so Many Nerve Cells?” In Parkinson's and Alzheimer's Today: About Neurodegeneration and its Therapy ,vol.1,no.3 ,pp. 1-26,2022. DOI: https://doi.org/10.1007/978-3-662-66369-1_1
M. A. Akbari,, M. Zare, R. Azizipanah-Abarghooee, S. Mirjalili, and M. Deriche, “ The cheetah optimizer: A nature-inspired metaheuristic algorithm for large-scale optimization problems” Scientific reports, vol.12 .no.1,pp. 109-153,2022. DOI: https://doi.org/10.1038/s41598-022-14338-z
M. H. K. Roni, M. S. Rana, H. R. Pota, M. M. Hasan, and M. S. Hussain, “ Recent trends in bio-inspired meta-heuristic optimization techniques in control applications for electrical systems: A review” International Journal of Dynamics and Control, vol.15,no.1,pp.1-13,2022.
S. Mirjalili, and A. Lewis, “ The whale optimization algorithm” Advances in engineering software,vol. 95, no.1,pp.51-67.,2016. DOI: https://doi.org/10.1016/j.advengsoft.2016.01.008
G.Sharma, S. Bala, and A. K. Verma , “ Security frameworks for wireless sensor networks-review” Procedia Technology, vol.6, no.1 pp.978-987,2012. DOI: https://doi.org/10.1016/j.protcy.2012.10.119
Fadhil, A. M., Jalo, H. N., & Mohammad, O. F. (2023). "Improved Security of a Deep Learning-Based Steganography System with Imperceptibility Preservation". International journal of electrical and computer engineering systems, 14(1), 73-81. DOI: https://doi.org/10.32985/ijeces.14.1.8
S . Rajashree,, and R. Sukumar , “ CBC (Cipher Block Chaining)-Based Authenticated Encryption for Securing Sensor Data in Smart Home” Smart IoT for Research and Industry, vol.3,pp.189-204,2022. DOI: https://doi.org/10.1007/978-3-030-71485-7_12
R. K. Meyers, and A. H. Desoky, “An implementation of the Blowfish cryptosystem”In IEEE International Symposium on Signal Processing and Information Technology ,pp. 346-351,December,2008. DOI: https://doi.org/10.1109/ISSPIT.2008.4775664
J. Zhang, and P. Xia , “ An improved PSO algorithm for parameter identification of nonlinear dynamic hysteretic models” Journal of Sound and Vibration, vol.389,.no.1,pp 153-167,2017. DOI: https://doi.org/10.1016/j.jsv.2016.11.006
J. McCall, “Genetic algorithms for modelling and optimisation” Journal of computational and Applied Mathematics, vol.184,no.1, pp.205-22,2005. DOI: https://doi.org/10.1016/j.cam.2004.07.034
H. M. Abdual-Kader, D. S. A. Minaam, and M. M. Hadhoud, “ Wireless network security has no clothes” In 2010 The 7th International Conference on Informatics and Systems (INFOS), pp. 1-8, March,2010.
Chosen-Ciphertext Attack. Accessed: Sep. 2021. [Online]. Available: https://en-academic.com/dic.nsf/enwiki/63077
Singh, M., & Singh, A. K. (2023). "A comprehensive survey on encryption techniques for digital images". Multimedia Tools and Applications, 82(8), 11155-11187. DOI: https://doi.org/10.1007/s11042-022-12791-6
Inayat, U., Zia, M. F., Mahmood, S., Khalid, H. M., & Benbouzid, M. (2022). "Learning-based methods for cyber attacks detection in IoT systems: A survey on methods, analysis, and future prospects". Electronics, 11(9), 1502. DOI: https://doi.org/10.3390/electronics11091502
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2024 Omar Hisham Rasheed alsadoon

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.
Deprecated: json_decode(): Passing null to parameter #1 ($json) of type string is deprecated in /var/www/vhosts/ijser.aliraqia.edu.iq/httpdocs/plugins/generic/citations/CitationsPlugin.inc.php on line 49









